Laos
- Dettagli
- Categoria: Projects
- Pubblicato Domenica, 30 Settembre 2012 17:43
- Scritto da Giampiero Gabbiani
- Visite: 5128
LAOS stands for Linux Auto Operator System, it is a passive automation system for the Linux OS.
I needed a way to trigger some actions in responce to some events from the syslog. Since I wasn't able to find any, I decided to write by myself. Basically it is possible to setup a number of regular expressions that are match against any message arriving to the daemon through the syslog protocol, and associate to each of them an arbitrary number of commands to be executed on the Linux system. The tool is written in C++, according to the recent C++11 enhancements, and thought to be run on Linux systems.
Usage example:
The combination of a regular expression and a collection of commands defines a laos rule. It is either possible to pass or construct the commands to be executed combining pieces of the message that triggered the rule.
"object" : {
"class": "collector::Rule",
"name" : "DENY",
"continuation": false,
"description" : "Notify a DENY from the firewall",
"expression" : "RULE \\d -- DENY IN=.*SRC=(\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}).*PROTO=(TCP|UDP).*DPT=(\\d{1,6}).*",
"command" : [
"exec" : {
"class" : "xsystem::Action",
"command": "logger -t laos -p local0.notice \"Destination is ${MATCHES[1]}\""
},
"notify" : {
"class" : "xdbus::Action",
"summary": "Firewall DENY",
"text": "${MSG_HOSTNAME} DENY source IP ${MATCHES[1]} PROTO ${MATCHES[2]} PORT ${MATCHES[3]}"
}
],
"conditionals" : [
"name": "MSG_HOSTNAME", "value": "athena"
]
}
the 'expression' element in the json config file, defines a simple rule for matching any message like the following:
Aug 5 07:48:10 athena kernel: [ 606.162477] RULE 6 -- DENY IN=virbr0 OUT= MAC= SRC=192.168.122.1 DST=192.168.122.255 LEN=140 TOS=0x00 PREC=0x00 TTL=64 ID=0 DF PROTO=UDP SPT=17500 DPT=17500 LEN=120
In the regular expression match the ip address will be held in the pseudo-variable array MATCHES[1], so the first of the 2 commands that will be executed
logger -t laos -p local0.notice "Destination is ${MATCHES[1]}"
will be expanded in
logger -t laos -p local0.notice "Destination is 192.168.122.255"
while the second command (an invocation of a DBus signal) - assumed that the corresponding host in the received syslog message is 'athena' will have the text attribute that will change from
"${MSG_HOSTNAME} DENY source IP ${MATCHES[1]} PROTO ${MATCHES[2]} PORT ${MATCHES[3]}"
to
"athena DENY source IP 192.168.122.1 PROTO UDP PORT 17500"
and it will emit a DBus signal on the system bus with the above text message.
Of course you can build whatever command you need.
New Architecture
Below the functional architecture of the release currently released.
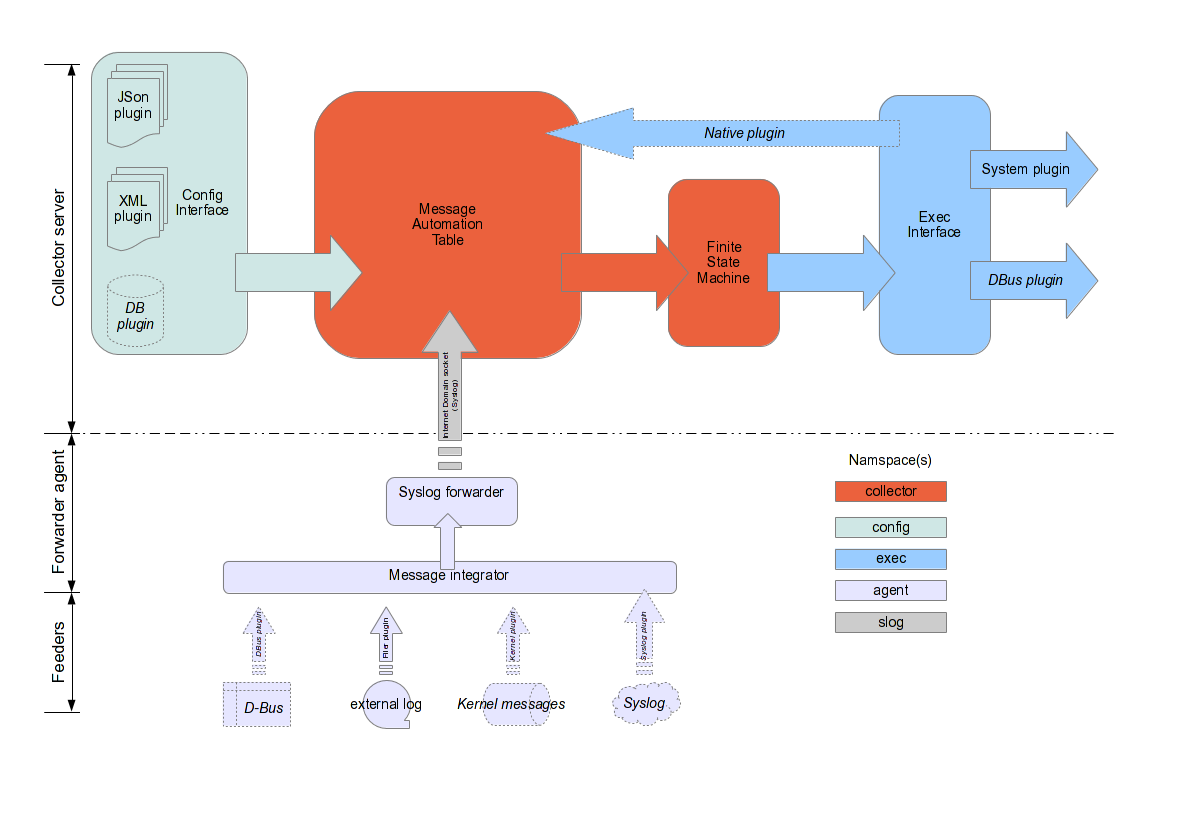
New features
- ruleset persistance [config]: the ruleset are saved in an XML or JSON format;
- DBus plugin [exec]: the DBus plugin has been developed and in conjunction with a userspace daemon, is able to notify the desktop users of the relevant events/messages;
- Collector [collector]: it uses a plugin interface for the exec namespace
- Agent [agent]: uses a plugin input interface so it is potentially able to send the collector messages for further automation from whatever source (D-Bus, log files, Kernel ring-buffer, Syslog)
References
SourceForge LAOS download




